This article was originally published by Security Magazine on June 25, 2019.
Risk quantification has long been an imperative topic for security leadership, but now more than ever, boards of directors and C-Suite executives are acutely invested in how their organizations are performing from a security risk perspective. Publicity garnered from cyber events is at a greater scale than has ever been seen, as are the liabilities. While each level of leadership is playing for the same team, the focus and methods in which each comes to a “win” can be entirely contrasting. This begs the question, how can boards, the C-suite, and security leadership all get what they want in terms of quantifying risk, while ultimately working together for the long-term benefit of the business?
As we’ll see in more detail, quantifying risk not only allows security leadership to build a stronger, more holistic security program, but it’s a key step in acquiring proper security funding as well.
Start with the Inherent Risk
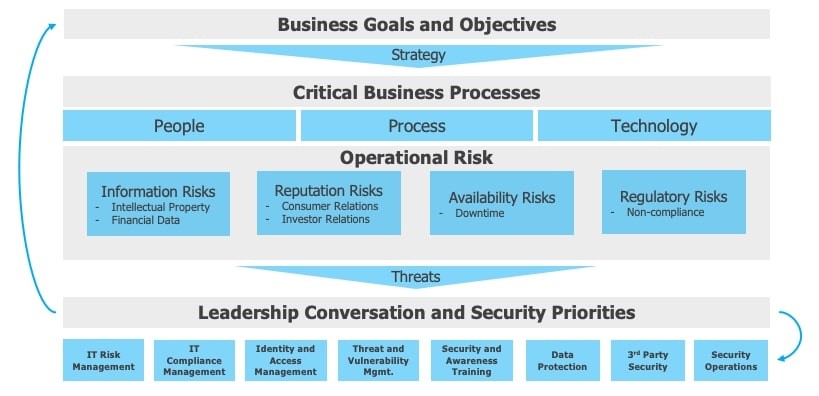
The first place to start in getting on the same page is to communicate a universal understanding of the security risks to an organization’s business objectives. This needs to be an ongoing conversation, as the risk landscape is ever-changing. For each business, this is always a little unique, because of the diverse verticals within different industries.
For example, an E-commerce company’s main operational risk may fall under “Availability Risks”, since their service not being available to consumers has immediate and measurable impact. However, a pharmaceutical organization’s priority most likely wouldn’t be availability of inventory, but rather “Information Risks”. The most valuable asset to their organization might be research and development around new drugs, therefore their greatest risk may be the loss of this intellectual property. Business-aligned conversations of this nature are the crucial component of ensuring buy in from senior executives as well as a prioritized and cost-effective security program.
The maturity of the business security program also needs to be frequently evaluated in order to remain relevant, or in some cases, gain relevancy. By comparing and analyzing the threat landscape, inherent risks of your business, and the security program maturity, leadership will be able to determine where any residual risk resides. Addressing residual risk with security program improvements is how to make meaningful risk reduction.
Respect Priorities
The CEO’s focus will typically have to do with the bottom line, as well as helping to manage public opinion and perception of the organization. As for matters of cybersecurity, this means that they will usually be more interested in the details around where their security programs reside, as well as making sure the program is as cost-effective as possible. Because they’re the ones “on the hook” for meeting regulatory requirements, they’ll want to be updated on any developments in their industry. The rest of the C-Suite will also be very interested in how they measure up against their industry peers and competitors.
While the destination is the same, the route of the conversation is going to be much different when speaking to the board. Compared to the C-Suite, an organization’s board of directors is going to want a much more succinct report on how the security program is operating. The level of depth and content is going to be much lower, since most boards are not typically as tech-savvy and have many business matters to decide, which is their primary role. They’re usually up-to-speed on existing industry and government regulations, but they should be kept in communication regarding the constant onslaught of new ones coming down the pipe.
This requires the cooperation of several different departments (CISOs, Legal, Data Privacy) in order to stay up-to-date. The board sees breaches in the news just as often as the rest of us, and they simply want to know how well-protected the company is against these threats.
Regardless of how the amount and detail in the information is shared, it should always stem from the same body of information: Where are our security gaps? Are they properly prioritized? How much will it cost to close any gaps?
Be Proactive with Security Framework Communications, and Tie Proposals Back to Business Objectives
For security leadership, a common hurdle in acquiring appropriate security funding stems from not having a common security framework report available. A simple summary explaining “This is where we are, and this is where we need to be” regarding their security program is often all it takes, and the mechanism for demonstrating this is commonly lacking in most organizations.
When speaking to the C-suite, security leaders have to be able to communicate security funding needs in terms of the overall business goals and objectives. Understand what risks threaten which business goals and objectives, and how additional funding will address those gaps. As a security leader it’s easy to get caught in the trap of over-explaining the security program at a technical level. In order to establish a holistic program, it’s critical to ensure that the explanation doesn’t lack in how the business objectives are supported.
The ideal way to pitch a security program to organizational leadership is always going to be: Business Goals & Objectives – Business Processes – Existing Operational Risks – Proposed Solution to Risk Gaps. Security leaders are also obligated to educate C-Suite and board members on the impact of being compliant with any and all regulations, such as HIPAA and PCI, as well as what the impact of being out of compliance could be.
The “Holy Grail” of Security Funding
“Knowledge is a process of piling up facts; wisdom lies in their simplification” – Martin H. Fischer
The key to successfully acquiring security funding often lies in simplicity. The temptation to over-communicate technical information is rampant, and often causes even well-seasoned CISOs to trip over themselves during meetings with business leadership.
Make sure that your message on the security program demonstrates to the board and C-Suite that you understand what the business goals and objectives are, and that you’ve crafted a plan that mitigates any of their risks in the most cost-effective way possible. This is the “holy grail” of acquiring the funding that your security program needs.
Jason Rowland is Vice President, Consulting Operations at Alagen. With more than 20 years of information security experience, he has led teams driving tailored solutions in the areas of compliance, security assessment, security operations, as well as major incident response and remediation efforts for Fortune 500 corporations.